
[IT168 information] Apple's iPhone7/iPhone7 Plus and iOS10 come as expected, iOS10 brings a lot of updates, the use experience has indeed been improved, but there is no revolutionary feeling. iOS has been developed for so many years, Apple has spent a lot of effort on iOS, but compared to the Android contending, Apple's iOS is a bit restless, many features on the Android phone iOS has delayed to follow up, not even In particular, some security features, iOS is not as good as Android. Here we take a look at the lack of iOS security features.

â–² Android has already done a lot of iOS10 security features
The iOS10 system's security interface was opened to the public for the first time. This is already an improvement for Apple. This allows third-party mobile security software to implement harassment and interception functions. Apple is only opening the interface and does not implement security functions in the system. These are harassment interceptors. The function was given to a third-party app. In addition, Apple is also very inadequate in terms of other mobile phone security. For example, Apple has been locked out of events in recent years, iMassage spam, etc. Apple has not given a good solution.
Telephone harassment interception
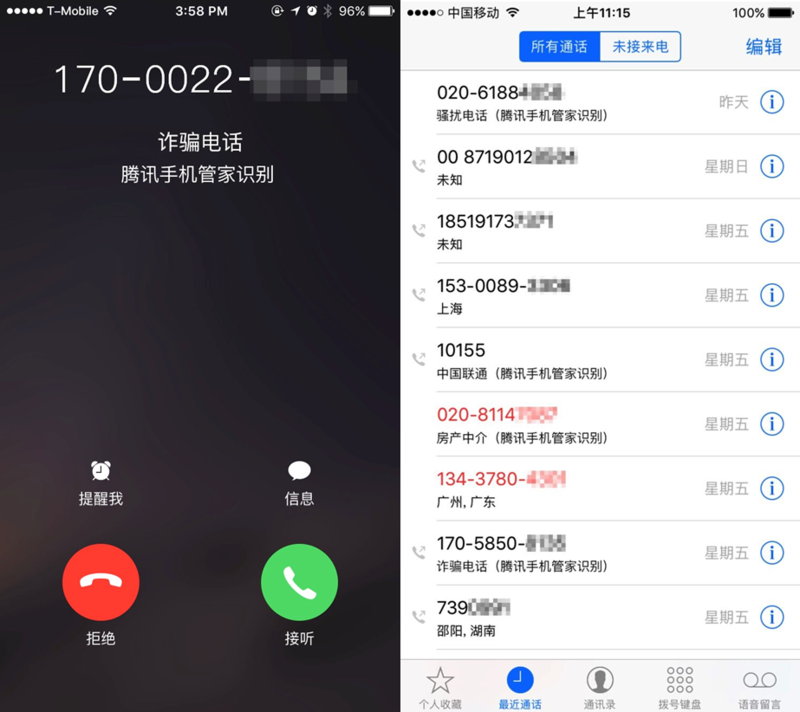
â–²iOS phone harassment blocking (based on third-party applications)
As mentioned earlier, the harassment blocking function of iOS is implemented through a third-party APP. iOS just opens an interface, and Apple gives security applications to third-party applications. Apple officials do not perform harassment blocking functions on their own. The harassment blocking feature is actually very simple to implement. A large cloud database of harassing phone numbers can be implemented. However, Apple's mobile phone is not just aimed at Chinese users. It is indeed difficult to establish a large database for global harassment interception.
Spam blocking
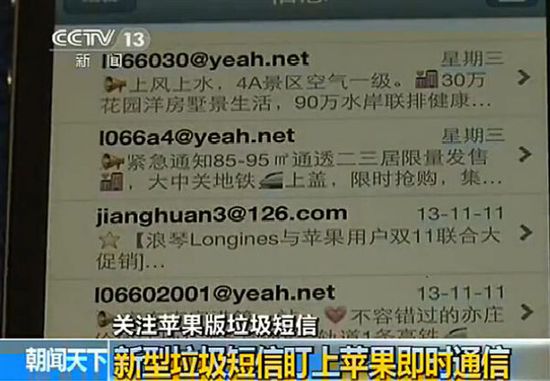
â–² CCTV bombards iMassage spam
Users who have used iPhone will receive iMassage junk messages. Even some users will receive several iMassage messages a day. Internet-based iMassage can send information for free, greatly reducing the cost of transmitting harassment information, and adding a large base for iPhone users. iMassage became the hardest hit spam. iMassage can be set to not receive non-contact iMassage information, but such a feature does not cure the symptoms. There is also no way to intercept mobile SMS spamming iOS. iOS basically does not have spam SMS interception.
Pseudo base station identification

â–² Pseudo base station
In China, pseudo-base stations are increasingly serious, and many users receive fraud information sent by pseudo-base stations. With the discovery of Android mobile phone security technologies, pseudo-base station identification functions have been implemented on Android phones, and information sent by pseudo base stations can be directly blocked. , protect the safety of Android mobile phone users. However, the pseudo-base station function is still not implemented on the Apple mobile phone. For many Apple users, the pseudo-base station SMS can still be received and is subject to harassment by the pseudo base station.
Virus killing
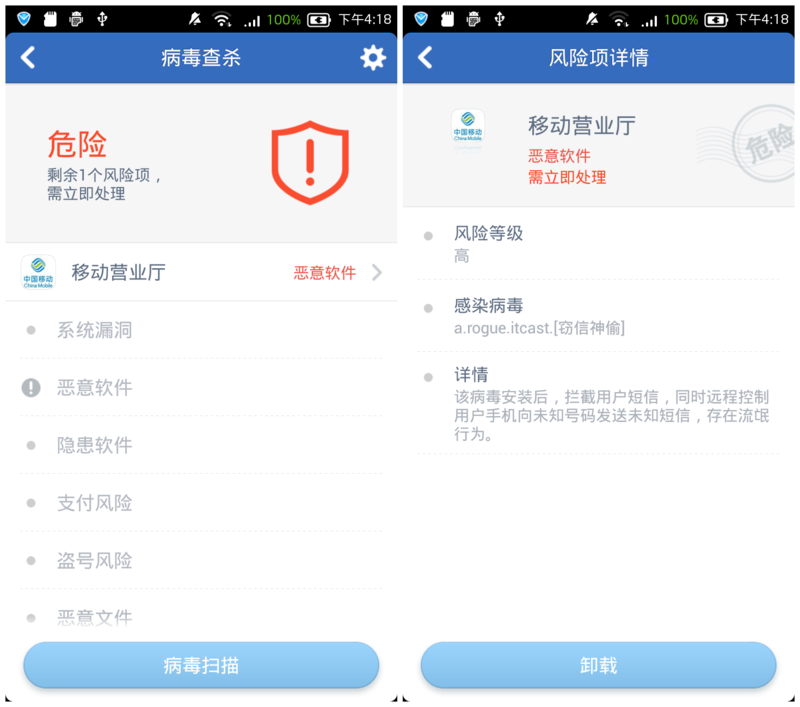
â–² Android mobile virus killing
Although iOS is a closed system, there are also users who like jailbreaking, and even some apps or websites attack the system through system flaws. In fact, large-scale iOS attacks and virus infections have not yet occurred, but this is also a security risk for users. Users can only install third-party applications to protect their own information security. Looking at the domestic mobile phone manufacturers, and even some international brands of Android phones, the virus killing function has long been integrated into the system, in this regard, Android phones do better than Apple.
privacy protection
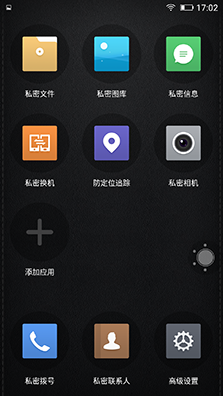
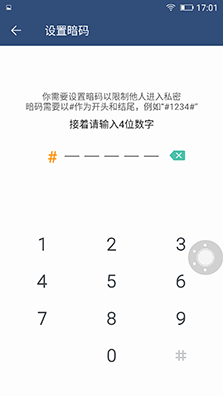
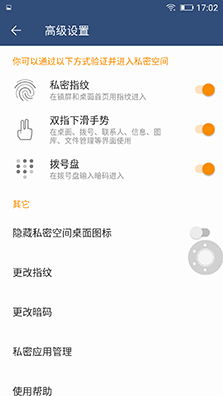
â–² Privacy Space on Android Phones
Apple's iOS provides very limited user privacy protection. Only applications based on fingerprint encryption are used. This is very insufficient for privacy protection for business people. Android phones already have privacy protection functions on many business phones. They can encrypt contacts, encrypt applications, encrypt files, and even use private spaces to store private files and some private files. Important information.
Cell phone is held hostage
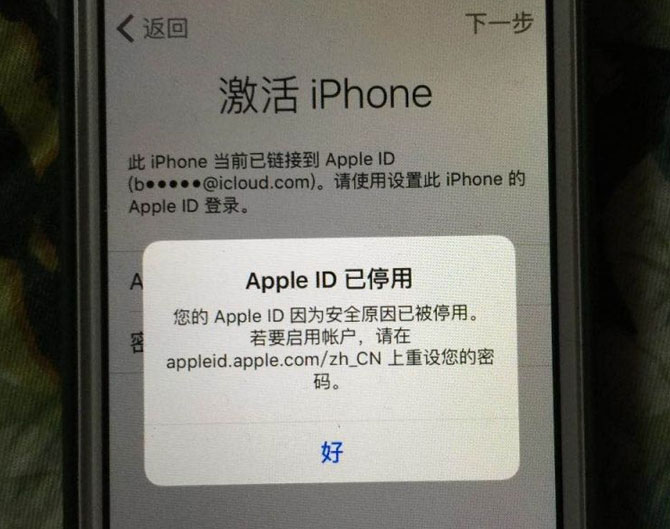
â–² iPhone is held hostage
In recent years, a lot of news that the iPhone was locked appeared. The Apple ID on the iPhone was stolen and the phone was locked. This incident also highlighted some defects of the Apple ID. Apple iPhone is based on Apple ID binding, users can find the phone through Apple ID, download applications, etc., but the scope of Apple ID application is too large, not only on the iPhone, the user needs other Apple services Apple ID, Apple's protection for Apple ID is too little, the risk of leakage of the user's Apple ID is very large, Apple ID leak allows criminals to lock the user's iPhone, the user blackmail. Although there are bound accounts on Android phones, they are only bound to their own mobile phones. Basically, Android phones are not used in other places. The risk of natural leaks is low, and the Android phone is dependent on user accounts. Without Apple's high, it also avoids cell phone being held hostage.
Summarize: Androids with a hundred schools of thought contend and rest on their laurels

â–² Jinli M6
In terms of system security, many Android phones have already achieved very rich mobile phone security features, especially for mobile phones targeted at political and business people, harassment interception, virus killing, and privacy protection. These basic mobile phone security features are already available on Android phones. On the development for a long time, but Apple still does not iOS. Further, such as the Jinli M6/M6 Plus to achieve pseudo-base station identification, private space, green calls these advanced mobile phone security features, iOS would not want to think. Although iOS is a closed system, but security issues can not be ignored, although Apple continues to update iOS, but the security update is less market, which is also a political and business people gradually abandoned the iPhone.