introduction
With the rapid development of the two-way transformation of digital TV networks, the conditional access system under the traditional one-way broadcast network environment has been unable to adapt to the new two-way network environment and business model. In order to further promote the rapid development of the digital TV industry, there is an urgent need to develop a security solution adapted to the two-way DTV network environment and business model to meet the operational and security needs of the two-way DTV business of digital TV.
In a two-way DTV network environment, there are two transmission channels between content publishers and end users. One transmission channel is a traditional one-way broadcast HFC channel, and the other is a two-way IP channel added after the two-way transformation of a digital TV network, such as Figure 1. In the two-way DTV service implementation, the program content is packaged into an MPEG TS stream and sent to the end user in a broadcast manner. The end user and the content provider complete the authentication and authorization and license application through the IP channel.
This paper proposes a two-way DTV security solution based on digital rights management (DRM) technology, which can achieve end-to-end secure transmission and storage of two-way DTV digital content, and can control the use of digital content rights.
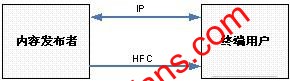
Figure 1 Two-way DTV network structure
Introduction to DRM
DRM technology can realize the description, identification, protection, monitoring and tracking of digital content, so as to protect the digital content intellectual property throughout the life cycle, and can realize the end-to-end secure transmission and storage of digital content, and can Realize the use control of digital content rights.
There are two main types of technology to achieve DRM: one is digital watermarking technology, and the other is data encryption technology. Digital watermarking technology is not yet mature, and can only be used for forensics or tracking after piracy is discovered, and cannot be prevented in advance. DRM technology with data encryption as the core, the core idea is to encrypt digital content, only authorized users can get the key to decrypt the content.
At present, most companies at home and abroad and research structure of DRM system use technology based on data encryption. This paper also proposes an effective copyright protection security solution for two-way DTV services based on data encryption technology, combined with digital signatures and certificate authentication technologies, which can achieve management control and copyright protection of two-way DTV business digital content.
solution
The two-way DTV DRM security solution proposed in this paper, combined with the certificate authentication system (PKI / CA), issues digital certificates for terminal devices and front-end servers, and uses digital certificates to identify and identify the entities in the authentication system. Establish a trusted trust system between users and users; design and implement a multi-layer key system, use asymmetric cryptographic algorithms for identity authentication, secure distribution and negotiation of content keys, and use symmetric cryptographic algorithms to encrypt digital content It is a ciphertext of media files, and distributed to end users through business models such as live broadcast and on-demand, and controls to ensure the reasonable use of digital content on the terminal.
system structure
The system architecture of the two-way DTV DRM security scheme proposed in this paper is shown in Figure 2:
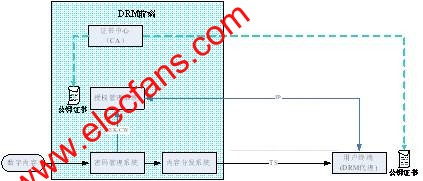
Figure 2 Two-way DTV DRM system architecture
The two-way DTV DRM security solution proposed in this paper consists of the following modules:
Certificate Center (CA): issue digital certificates for front-end authorization management systems and terminals, and establish a PKI-based trust system; terminals and authorization management systems complete two-way identity authentication and secure channel establishment through certificate exchange and key negotiation;
Authorization management system: generate licenses for the terminal, and verify the identity of the terminal, and authorize the terminal security;
Password management system: generate various keys and realize content encryption; online live encryption for live content; offline pre-encryption for on-demand content;
DRM agent: A trusted entity in the device that implements permission and restrictions on content and controls content usage. Operate digital content strictly in accordance with authority;
Content distribution server: store and manage encrypted digital content, and distribute content according to different business models;
Key system
This paper proposes a two-way DTV DRM security solution combined with PKI asymmetric cryptosystem to establish a multi-layer key system.
The top two layers of the key system are the device public and private key pair and user key. For terminal devices such as set-top boxes, a public and private key pair is generated during initialization. The private key is stored securely in the terminal, and the public key is sent to the front-end CA center through a secure channel to apply for a terminal certificate, so that the server maintains the terminal's device public key or certificate. When distributing a smart card to a user, it is necessary to initialize the smart card and write the user key or domain key in the smart card, and the server also maintains the correspondence between the user key / domain key and the smart card.
For keys that directly encrypt content, different key systems are used according to the type of content:
When the data content is a TS stream or a stream file, the key scheme adopts a CAS-like real-time scrambling key system: first use the control word (CW) to scramble the content, and then use the service key (SK) to encrypt the transmission CW, encryption The CW and program control data are encapsulated in ECM and broadcast with the content data. The service key is encrypted by the user key (PK) / domain key (DK), and can be encapsulated and broadcasted in the EMM, or delivered end-to-end through a bidirectional IP channel, as shown in Figure 3.
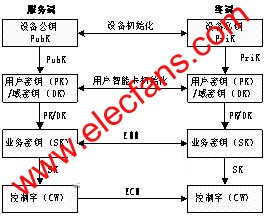
Figure 3 Streaming media key system
For non-TS stream data, such as images, animation data, etc., this scheme uses a symmetric key encryption key system, using content encryption key (CEK) to directly encrypt content data, the content encryption key is encapsulated in the rights object to use the user The key (PK) / domain key (DK) encryption is delivered end-to-end through a bidirectional IP channel, as shown in Figure 4.

Figure 4 Non-streaming media key system
Data encapsulation
This solution uses different data encryption and encapsulation methods for different content types. For TS streaming media content, encrypt TS packets one by one, and only encrypt 184 bytes of TS packet load, and directly multiplex with other TS streams for broadcast distribution; for non-TS stream files (such as animation, picture content), you should Continuous encryption, packaged into TS stream cyclic broadcast.
Business Process
The two-way DTV DRM security solution proposed in the text can support multiple business models such as live broadcast and on-demand. Different business models and specific business processes are different; for live broadcast services, encryption methods and business processes are similar to traditional unidirectional network TV broadcast services, in which digital content is scrambled in real time, and scrambling control words CW encryption are encapsulated in ECM In the service key encryption and packaging EMM, the scrambled digital content is broadcast and distributed together with ECM and EMM. Of course, EMM can also be distributed online via a two-way IP network.
This article takes the on-demand service as an example to briefly explain the processing flow of the service:
Digital content is pre-encrypted in the password management system, and the encryption key is sent to the authorization management system to generate a permission license, and the encrypted digital content is sent to the content distribution server; when the user orders digital content on the terminal, the user first sends the authorization management system Request a permission license for this digital content. At this time, it is necessary to perform two-way identity authentication on the terminal and the authorization management system, and negotiate the session key to establish a secure connection between the two parties; the authorization management system issues an authorization license for on-demand content to the terminal through connection protection, and also requires the content distribution server to The terminal broadcasts the content on demand; the terminal DRM agent verifies the validity of the authorized license, strictly operates the content in accordance with the permissions and restrictions in the license, and provides services for users.
Security analysis
Trust model
The two-way DTV DRM security solution proposed in this paper adopts a PKI-based certificate authentication system. Each terminal device needs to apply for a certificate from the certificate center when it is initialized. The front-end server verifies the identity of the terminal agent by verifying the validity of the terminal agent's certificate, which can achieve trust between the system entities;
Content security and authorization security
In a two-way DTV system, digital content is delivered to terminals through a broadcast channel, and all terminals can obtain these digital contents. Therefore, it must be ensured that the digital content is not accessed by unauthorized parties, and can only be properly accessed by authenticated and authorized users in accordance with the authority. In the scheme proposed in this paper, digital content is encrypted, such as streaming media content using CW scrambling, non-streaming media content using content encryption key encryption, and the encryption key is unique to each content object, and the copyright object carries The encryption key is also encrypted and encapsulated, and can only be accessed by the designated terminal. This can achieve content security and authorization security, and effectively prevent media content from being unauthorized to be cracked, thereby protecting the legitimate rights and interests of content providers and users.
Secure connection
In the two-way DTV service, the terminal needs to request the authorization management system to obtain a permission license online. This requires avoiding impersonating the terminal or the authorization management system illegally to avoid authorization to the illegal terminal or loss of sensitive user information. In this solution, the terminal and the authorization management system establish a secure connection to prevent such attacks. The process of establishing a secure connection is first of all two-way identity authentication, that is, through the exchange of digital certificates, the two parties verify the validity of the other party ’s digital certificate to verify the legality of the other party ’s identity, which can avoid attacks that impersonate the terminal or authorization management system. The two parties then negotiate a temporary session key, such as using the DH key agreement protocol, so that the permission license is encrypted and transmitted to the terminal, and the attacker cannot obtain the end user's license. This guarantees the security of the terminal's online request to obtain an authorization license from the authorization management system.
in conclusion
This paper proposes a two-way DTV DRM security solution. Security analysis shows that it can meet the security requirements of two-way DTV digital content protection. However, as the types of services in the two-way DTV system increase, especially the deployment and operation of a large number of value-added services, the two-way DTV system has more complex security requirements, and the support of the two-way DTV security solution for all services should be further considered to achieve uniformity as much as possible Business security.
With the rapid development of the integration of the three networks, various Internet public network services, such as network video, Internet TV, and video-based Internet services, will gradually penetrate into the radio and television network. Most of these Internet video and audio services are provided to users free of charge, and do not use content or program authorization as a means of profit. Therefore, without complete business protection and content protection, end-to-end security guarantees for content cannot be achieved. However, in the broadcast network, digital TV, as an important publicity window, must achieve comprehensive security control of the audio and video content therein, and needs to achieve the "manageable and controllable" advocated by NGB, so the video and audio business of the broadcast network It is necessary to follow the security system under the broadcast and television network to create a safe and harmonious TV broadcasting environment.
LED Street Light Heatsink, LED Street Light Housing, LED Street Light Parts
LED Street Light Heatsink
LED Street Light Heatsink, LED Street Light Housing, LED Street Light Parts
Shenzhen Ri Yue Guang Hua Technology Co., Ltd. , https://www.ledlightinside.com