WSN (Wireless Sensor Network) is the product of the combination of three technologies: sensor, communication and computer. South WSN integrates the logical information world and the objective physical world together, changing the interaction between human and nature Has broad application prospects. Wireless sensor networks have many characteristics that are different from traditional networks, such as severe energy limitation and frequent topology changes. Therefore, the design of the WSN network protocol is very different from the design of existing various network protocols, and therefore faces various new challenges. Among the many protocols in the protocol stack, the network layer routing protocol algorithm as a key technology has become the focus of current research.
Routing protocol for wireless sensor networks
There are many classification standards for WSN routing protocols, so there are also various classification methods for routing protocols. According to the different working principles of routing protocols, routing protocols are divided into two types, and the typical routing protocols of each type are analyzed.
2.1 Plane routing
Plane routing believes that each node in the sensor network has the same function and equal role. The node may actively report its event detection results to other nodes, or other nodes send query information to the node that detects the event, and the data is transmitted through multiple nodes The multi-hop routing cooperative forwarding is completed. The information negotiation sensor SPIN (Sensor Protocols for InformaTIon via NegoTIaTIon) is the first data-centric algorithm in planar routing, which reduces data redundancy and energy consumption through a negotiation mechanism between nodes. SPIN is a data-centric routing algorithm based on a negotiation mechanism. SPIN first abstracts the characteristics of the data received by the node at a high level to form meta-data describing the characteristics of the data received by the node. Before forwarding the received data, node A uses metadata to negotiate with neighboring node B, and sends an ADV signal to determine whether node B needs the data (Figure la). If Node B needs the data represented by the metadata, it sends a feedback signal REO (Figure 1b). Otherwise, the ADV signal is discarded, and then node A forwards the data DATA to node B (Figure lc). After receiving the data forwarded from node A, node B adopts the same processing method as node A. First, use the metadata to negotiate with all nodes connected to it to send the ADV signal (Figure 1d). If there is a demand, the node will reply the REQ signal, if there is no demand, the ADV signal will be discarded directly (Figure 1e), and then Node B will send data DATA to all nodes that reply to the REQ signal (Figure 1f).
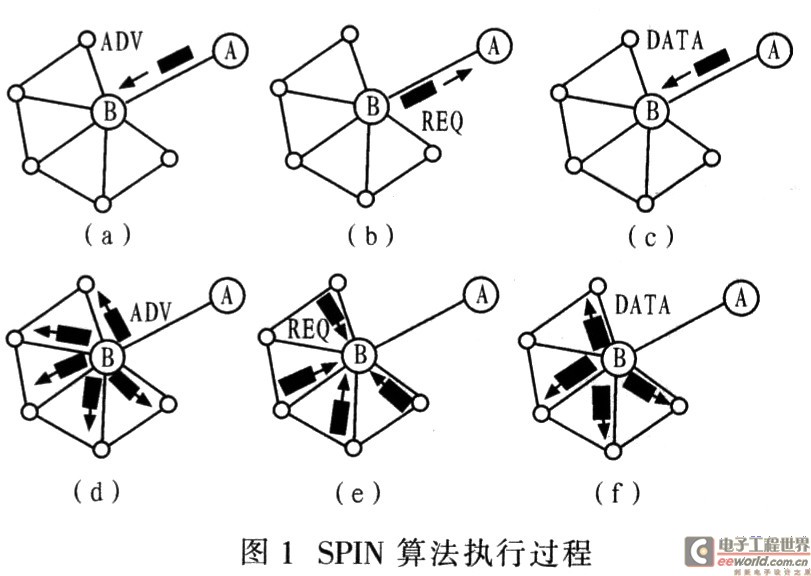
The SPIN algorithm does not clearly define the format of metadata. The specific format is related to the application. For example, the format of ADV and REQ can be specified in detail according to the specific application. In addition, when the topology changes, each node only needs to maintain the status of its neighbors within a local range, and does not need to broadcast the entire network, which not only saves energy but also reduces the requirements for the computing power of the node. This SPIN is called SPIN -1. However, SPIN-1 cannot guarantee the correct delivery of remote data. For example, the remote node needs data but the near-end node adjacent to the source node does not. The metadata representing the data is discarded at the beginning of forwarding, and no REQ reply is made. , Causing data delivery to fail. In order to solve this problem, an energy threshold mechanism is added on the basis of SPIN-2 and SPIN-1. Before delivering the data, first detect the energy of the neighboring node. If the energy value is lower than a certain threshold, it is considered that the node does not have sufficient capacity to complete the remote delivery task, and the data is forwarded to other neighboring nodes with sufficient energy. In addition, for different application situations, SPIN's other extended protocols, such as SPIN-BC and SPIN-RL, are specific to multicast networks such as sensor networks, and SPIN-PP and SPIN-EC are dedicated to traditional point-to-point networks optimization.
2.2 Hierarchical routing
Hierarchical routing (also known as cluster-based routing) was first created and applied to wired networks, and satisfies the efficient communication of large-scale networks. Therefore, the concept of hierarchical routing is also introduced into WSN, which is used to meet the low energy consumption and high efficiency communication of sensor nodes. In hierarchical routing, high energy nodes can be used for high energy consumption applications such as data forwarding, data query, data fusion, remote communication, and global routing maintenance; low energy nodes are used for low energy consumption such as event detection, target positioning, and local routing maintenance Application occasions. In this way, different applications are reasonably allocated according to the different capabilities of the nodes, so that the nodes can give full play to their respective advantages to cope with the large-scale network situation and effectively improve the survival time of the entire network. Hierarchical routing mainly includes two levels of routing: one is for selecting cluster head nodes, and the other is for routing. LEACH (low-energy adapTIve clustering hierarchy) is an earlier WSN-level routing algorithm based on clustering ideas. Compared with the traditional network where the energy of fixed gateway nodes is sufficient, the energy of nodes in WSN is limited, so the same fixed cluster head node cannot be used as a gateway. LEACH randomly selects a small number of nodes from WSN as cluster heads. Considering the balance of energy consumption of each node in the network, let other nodes that have not done cluster heads take turns as cluster heads, so that the network will not be caused by the exhaustion of energy by a few nodes The network is down.
The LEACH algorithm is divided into two stages: cluster head establishment and stable state. The former is the key to the realization of the LEACH algorithm, and the latter is the guarantee of data transmission. In the cluster head establishment phase, the node randomly chooses a value r (O
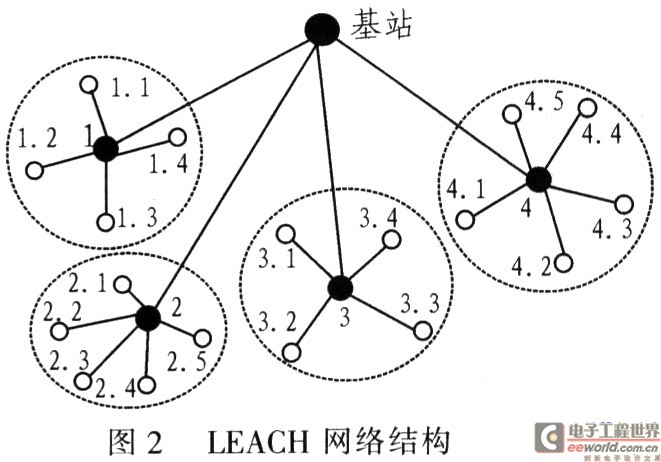
LEACH's clustering mechanism can reduce the overall energy consumption of the network and extend the network's survival time; adopt TDMA encoding between nodes in the cluster and CDMA encoding between the cluster head and the base station to ensure effective transmission of information; both data collection and cluster head nodes Periodically, the network is suitable for monitoring continuously changing events.
The network layer of the wireless sensor network is expounded, and the routing algorithm is taken as the main research line, and the two routing algorithms of WSN are analyzed in depth. The routing algorithm research mainly has the following difficulties: (1) Data fusion is performed at the network layer or application layer. The network layer mainly relies on routing algorithm coordination to discard redundant packets, reduce node energy consumption and improve data forwarding efficiency. (2) To ensure the reliability of data transmission and minimize the overhead of multi-path maintenance, the algorithm should not be too complicated. (3) For WSN, in addition to considering the situation when the node is stationary, node mobility also needs to be considered. If it is not a mobile tracking node, the radio frequency channel can generally be closed when the node moves. (4) The routing algorithm should handle the coordination between the nodes, even if the number of nodes is large, it can complete normal data forwarding, and will not cause failure in a short time. (5) For WSN with a large number of nodes, due to the randomness of the network topology distribution, some key nodes may consume more energy, while other nodes consume less energy, and the network load is unbalanced. Therefore, it is necessary to use the Lunan algorithm to strengthen the network load balance. (6) Due to the particularity of WSN, the energy consumption of nodes must be considered. Therefore, to study the WSN routing algorithm, we should reduce the energy consumption of the nodes as much as possible to extend the network survival time.
Introduction to Wireless Sensor Network Hardware Design
function ImgZoom (Id) // Re-set the image size to prevent the form from being broken {var w = $ (Id) .width; var m = 650; if (w <m) {return;} else {var h = $ (Id) .height; $ (Id) .height = parseInt (h * m / w); $ (Id) .width = m;}} window.onload = function () {var Imgs = $ ("content"). getElementsByTagName ( "img"); var i = 0; for (; iHigh Voltage Capacitor,Igh Voltage Variable Capacitor,High Voltage Electrolytic Capacitors,High Voltage Capacitor Leakage Tester
Yangzhou IdealTek Electronics Co., Ltd. , https://www.idealtekpower.com